The Power of Access Tokens and Refresh Tokens: A Guide to Secure Authentication
Access Tokens and Refresh Tokens: Safeguarding Security and Privacy in a Connected World
A token is a piece of data that serves as a representation or proof of authorization. It is typically used to authenticate and validate the identity of a user or a client application in order to grant access to certain resources or perform specific actions.
Access tokens play a crucial role in granting permissions and ensuring privacy in various settings. In this blog post, we'll explore an intriguing real-life example that showcases the significance of access tokens in the context of hotel access cards. We'll delve into how hotels have cleverly implemented a system with two cards—the access card and the refresh card—to bolster security and protect guests' privacy.
The Power of Access Tokens: Access tokens serve as the key to accessing specific resources or areas, providing a layer of protection against unauthorized access. To exemplify this concept, let's consider the scenario of hotel access cards.
Traditional Access Cards and Privacy Concerns: In the past, hotels provided guests with a single access card to open their room doors. However, if this card were misplaced or fell into the wrong hands, it would pose a potential privacy risk. Anyone possessing the lost access card could gain entry to the guest's room, compromising their personal space and belongings.
Introducing the Access Card and Refresh Card System: To address these concerns and bolster privacy, hotels have introduced a more secure solution: the access card and refresh card system.
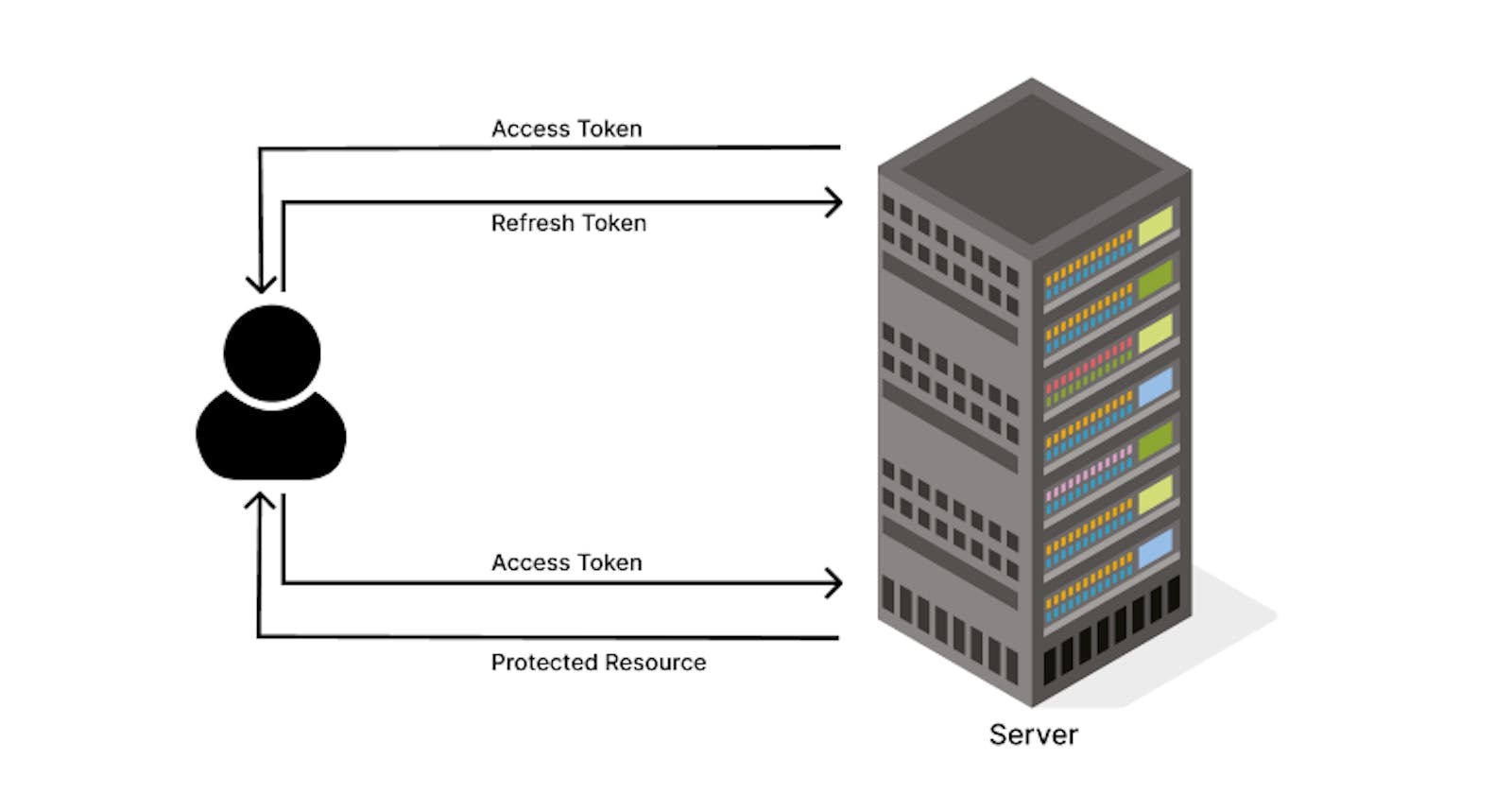
Access Card: The access card serves as the primary means of entry to the guest's room. It functions similarly to a standard access card, providing the convenience of easy door access during the guest's stay.
Refresh Card: In addition to the access card, hotels provide a refresh card to guests. The refresh card's purpose is to renew the access card periodically, ensuring its validity and enhancing security.
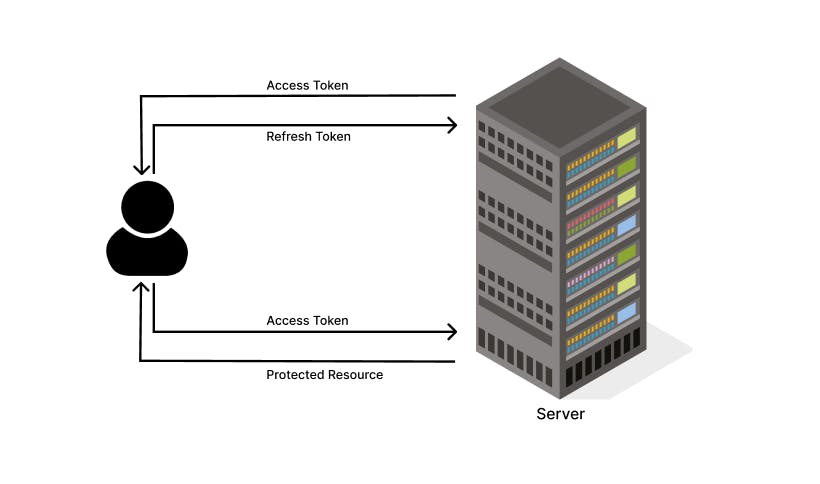
The Role of Expiry: To further mitigate the risks associated with lost or stolen access cards, the access card comes with an expiry date. This means that even if the access card is found by an unauthorized individual after being lost, its usability is limited. Once the access card expires, it becomes ineffective, preventing potential breaches of privacy.
The Refresh Card's Vital Function: The refresh card plays a vital role in the access card system. When the access card approaches its expiry date, the guest can use the refresh card to renew its validity. This process ensures that the guest retains secure access to their room throughout their stay, while also rendering any lost or stolen access cards obsolete once they reach their expiration.
Conclusion: Access tokens, such as the access card in the hotel context, are indispensable tools for ensuring privacy and security. By implementing a two-card system with an access card and a refresh card, hotels can effectively protect guests from unauthorized access and potential privacy breaches. The expiry feature of the access card and the renewability provided by the refresh card contribute to an enhanced level of security, giving guests peace of mind during their stay.
Remember, access tokens are not limited to hotel access cards. They are prevalent in various domains, such as digital authentication and authorization systems. Understanding their importance and the strategies employed to maximize security can help us appreciate the role access tokens play in safeguarding privacy in our interconnected world.
Please let me know which blog you would want to see next.